CEH
The popular CEH course from EC-Council is included in this training package.
The Certified Ethical Hacker (CEH) course, known as the Lawful Hacker, is one of the most prominent hacking and security courses in the world. In this course, students as white hat hackers will learn how to legally inspect network infrastructure to find security vulnerabilities. This course will help you assess the security posture of an organization to determine whether unauthorized access is possible.
Who is a legal hacker? Legitimate hackers or white hats are people who use their knowledge not for malicious purposes but to secure computer systems. By finding vulnerabilities and security flaws and reporting them, they solve the security problems of the company and organization and thus increase security.
It should be mentioned that practical laboratories have been designed for all the materials to help the practical learning of students as much as possible.
Prerequisites for participating in this course:
Complete mastery of Network+ and TCP/IP
Familiarity with Linux (installation of the operating system and basic use of the command line and basic commands)
Basic familiarity with network equipment such as Cisco and Mikrotik (ability of initial and basic configurations)
Topics presented in this course:
Module 01: Introduction to Ethical Hacking
Module 02: Footprinting and Reconnaissance
Module 03: Scanning Networks
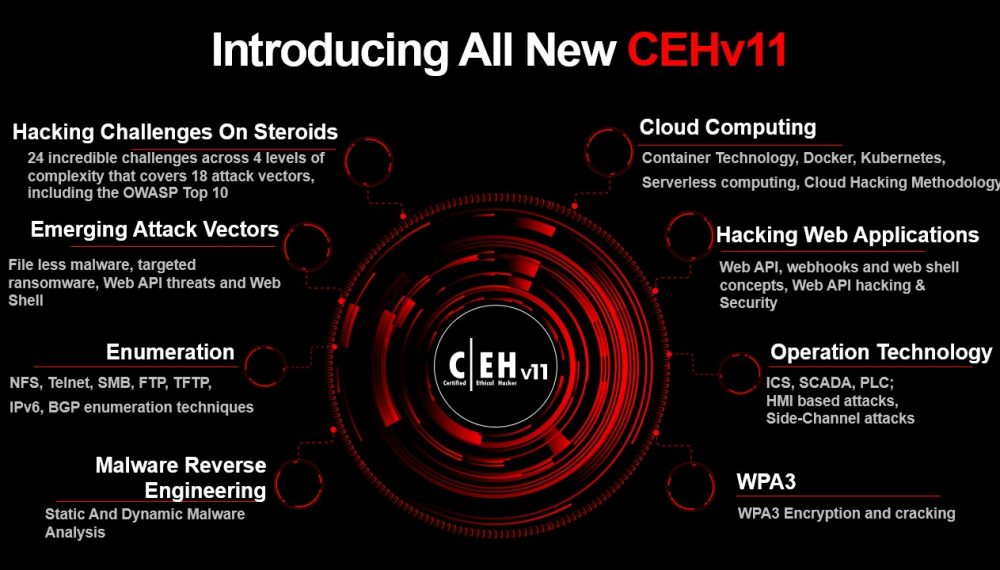
Module 04: Enumeration
Module 05: Vulnerability Analysis
Module 06: System Hacking
Module 07: Malware Threats
Module 08: Sniffing
Module 09: Social Engineering
Module 10: Denial-of-Service
Module 11: Session Hijacking
Module 12: Evading IDS, Firewalls, and Honeypots
Module 13: Hacking Web Servers
Module 14: Hacking Web Applications
Module 15: SQL Injection
Module 16: Hacking Wireless Networks
Module 17: Hacking Mobile Platforms
Module 18: IoT Hacking
Module 19: Cloud Computing
Module 20: Cryptography